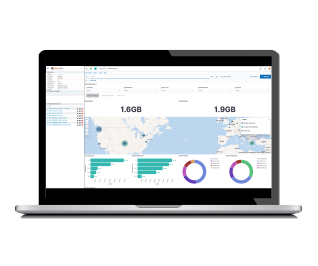
Full Packet Capture for Total Network Visibility
Retain weeks, months, or years of full-fidelity packet capture data across enterprise networks so your team never loses critical visibility.
Scalable Network Forensics & Visibility
SentryWire is a Full Packet Capture Appliance & Network Security Monitoring Platform with line rate capture and fast retrieval storage architecture which breaks through the performance, scalability and cost barriers of existing frameworks. SentryWire supports capture rates from 1Mbps to +1Tbps, while providing real-time logging, filtering and compression, allowing retention of network traffic for weeks, months and even years at price points that can be less than 50% the cost of other systems.
Network Security Monitoring Use Cases
Monitor industrial networks without agents or disruption
Reconstruct attacks with forensic-grade packet evidence
Identify stealthy threats hidden in encrypted traffic
Core Capabilities at a Glance
Full Packet Capture
Unlike basic sniffers that focus only on headers or metadata, SentryWire stores the entire packet stream for forensic replay, deep inspection, and extended historical analysis.
Powerful & Fast Search
Scale searches by leveraging distributed compute and storage, streaming results from PCAP data in near real time without impacting network performance.
Extended Timeline
Retain packet data for weeks, months, or years, giving analysts access to historical traffic long after other tools have cycled it out.
SentryWire is purpose-built for large, complex environments, including enterprise networks, federal agencies, and ICS/OT operators. The platform delivers high-fidelity full packet capture with integrated Network Security Monitoring (NSM), real-time and retrospective analysis, and built-in IDS capabilities. With long-term retention, powerful search, and cost-effective storage on commodity hardware, SentryWire gives security teams the visibility they need to investigate threats and maintain compliance at scale.
Built for Enterprise, Federal, and ICS/OT Networks
Why Full Packet Capture Matters?
An extended timeline of full packet traffic is critical because many advanced intrusions go undetected for months. Industry data shows it can take over 140 days to identify certain state-sponsored attackers. Without long-term, high-fidelity packet capture, security teams cannot accurately determine when an intruder entered the network, how they moved, or what data was accessed or exfiltrated.
Full packet capture provides the definitive forensic evidence required for incident response, threat hunting, and regulatory compliance. By supporting the visibility and retention requirements of today’s most demanding frameworks, SentryWire helps enterprises, federal agencies, and critical infrastructure operators maintain audit readiness and long-term network visibility.
SentryWire integrates with leading technology providers to extend the power of our full packet capture platform. Our partner ecosystem includes security monitoring tools, SIEM/SOAR platforms, IDS engines, forensic analysis solutions, and enterprise hardware providers, ensuring seamless deployment across federal, enterprise, and ICS/OT networks.
Industry-Leading Integrations & Partners
Contact Us
Whether you’re exploring full packet capture for the first time or looking to optimize your current network visibility, our experts are here to help.